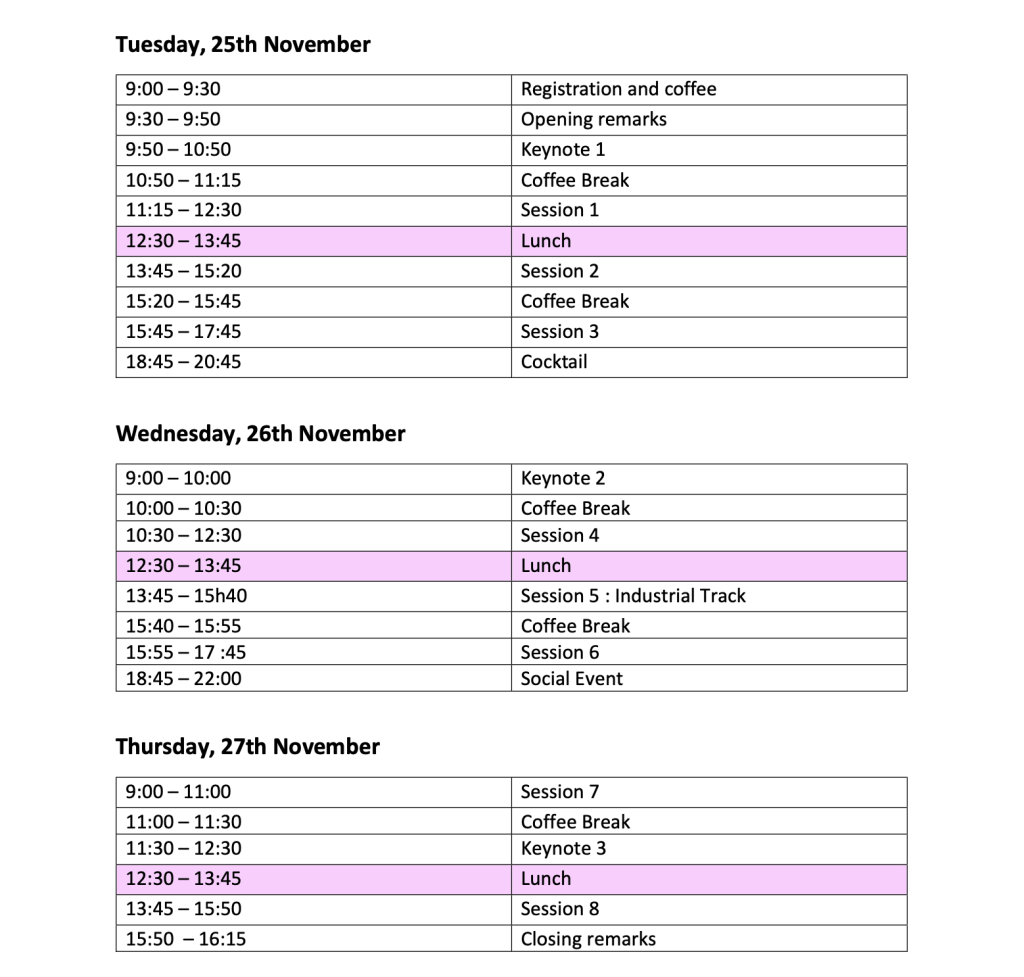
- Main FPS conference is to be held at IMT Atlantique from November 25th to 27th, 2025
- Main conference is accompanied by a one-day workshop on November 24th, 2025
- Afternoon workshop on women in cybersecurity (starting at 1:30pm) is open to FPS participants ; participation is free of charge
Download the detailed program here
Session 1: Security, Privacy, and Trust in Blockchain & Emerging Distributed Systems
Session Chair: Johanne Vincent
| Pierre Saha Fobougong, Mohamed Mejri and Kamel Aldi | "Towards A Pragmatic Selection Of Self-Sovereign Identity Security Measures : Exploiting Mitre Att&ck Graph And Multi-criteria Optimization" |
| Petr Dzurenda, Minh Tran, Mubashar Iqbal, Sara Ricci, Vaclav Stupka, Raimundas Matulevicius and Lukas Malina | "ForensicChain: Blockchain-based Secure Digital Forensic Investigations" |
| Jan Ariel Ocampo, Lejla Islami and Mina Alishahi | "Privacy-Preserving Federated Learning for IoT Intrusion Detection in 6G Networks" |
| Remi Barbier, Francoise Sailhan, Alexandre Reiffers-Masson and Loic Machado | "Scaling Blockchains with zk-Rollups: State of the Art and Implementation" |
Session 2: Cyber Resilience and Risk Management in Enterprise Architectures
Session Chair: Reda Yaich
| Francis Wanko Naa, Nora Boulahia-Cuppens and Frederic Cuppens | "Eliciting metrics and evaluating cyber resilience of a capability in multilayer enterprise architecture" |
| Arslane Fawzi Halilou and Natalia Stakhanova | "Predicting IoT Security Vulnerabilities from Device Specifications" |
| N'Famoussa Kounon Nanamou, Neda Baghalizadeh-Moghadam, Kéren A Saint-Hilaire, Thibault Leblanc, Nora Cuppens, Frédéric Cuppens and Anis Bkakria | "Real-Time Insider Threat Hunting Based on Dynamic Risk Indicators" |
| Babacar Mbaye and Mohamed Mejri | "Optimizing Resilience in IT Architectures : A Multi-Objective Ontology-Based Approach" |
| Barbara Carminati, Elena Ferrari, Christian Rondanini, Azhar Muhammad Shahid and Luca Clementi | "COBRA-Z: Collaborative Blockchain Risk Assessment for Zero Trust Architecture" |
Session 3: Formal Methods and Automated Analysis for Secure Software Systems
Session Chair: Kassem Kallas
| Yekatierina Churakova, Mathias Ekstedt and Larissa Schmid | "Vexed by VEX Tools: Consistency Evaluation of Container Vulnerability Scanners" |
| Alberto Tacchella, Jurij Mihelič, David Cerdeira, José Martins, Sandro Pinto, Bruno Crispo and Marco Roveri | "Towards a formal verification of the Bao Hypervisor" |
| Luis Soeiro, Thomas Robert and Stefano Zacchiroli | " Finding Software Supply Chain Attack Paths with Logical Attack Graphs" |
| Rémi Garcia, Paolo Modesti and Leo Freitas | "From provable models to provable implementations: translating Alice & Bob security protocols to F*" |
| Quentin Goux and Nadira Lammari | "Automatic Attack Script Generation: a MDA Approach" |
| Ludjina Benoit, Rim Ben Salem, Nora Boulahia-Cuppens and Frédéric Cuppens | "Mining Reliable ABAC Policies: A Specificity and Confidence-Aware Extension of Rhapsody" |
Session 4: ML and Intelligent Systems for Attack Detection and Trust Evaluation
Session Chair: Ranwa Al Mallah
| Antoine Rebstock, Yann Busnel and Romaric Ludinard | "A Grammar-Driven Approach to Model and Detect APT Attack Sequences" |
| Bastien Vuillod, Pierre-Alain Moellic and Jean-Max | "Watch Out for the Lifespan: Evaluating Backdoor Attacks Against Federated Model Adaptation" |
| Seán Óg Murphy, Utz Roedig and Cormac Sreenan | "Systematic Security Context Weighting for Trust Algorithms via AI/ML Model Performance Analysis" |
| Kobra Khanmohammadi, Pooria Roy, Raphael Khoury, Abdelwahab Hamou-Lhadj and Wilfried Patrick Konan | "WildCode: An Empirical Analysis of Code Generated by ChatGPT" |
| Miguel Silva, Daniela Pinto, João Vitorino, Eva Maia, Isabel Praça, Ivone Amorim and Maria Viamonte | "Binary and Multiclass Cyberattack Classification on GeNIS Dataset" |
| Bassirou Badiane, Valerie Viet Triem Tong and Yufei Han | "Towards Automated Botnet Threat Intelligence with Knowledge-Guided Large Language Models" |
Session 5: Industrial Track
Session Chair: Davis Espes
| Pierre Mahieux, Mouhamadou Bamba Sakho, Gouenou Coatrieux and Reda Bellafqira | "An Improved Paillier-Based Reversible Watermarking Scheme for 3D Models with Reduced Complexity" |
| Yeoh Wei Zhu, Shaltiel Eloul, Yash Satsangi, Imran Bashir and Sudhir Upadhyay | "Towards adoption of private distributed ledgers for capital markets" |
| Florence Sèdes and Brice Chellet | "Dynamic Multilayer Information System Cartography for Cybersecurity, Compliance and Industrial Governance" |
| Francesco Ferazza and Konstantinos Mersinas | "Socio-Technical Friction: An Emergent Grounded Theory of DevSecOps Challenges" |
| Tanja Pavleska, Giovanni Paolo Sellitto, Helder Aranha and Massimiliano Masi | "Secure-by-Design Architectures for Cooperative Intelligent Transport Systems" |
| Leonie Wolf, Samson Umezulike, Gurur Öndarö, Sebastian Schinzel and Fabian Ising | "Practical Evaluation of the Crypto-Agility Maturity Model" |
Session 6: Advances in Privacy-Preserving Cryptography and Secure Computation
Session Chair: Joaquin Garcia-Alfaro
| Yuan Liang, Giovanni Di Crescenzo and Haining Wang | "Sender-Efficient Identity-Based Encryption with Reduced Server Trust in the Key Curator Model" |
| Shohei Kaneko, Yang Li, Kazuo Sakiyama and Daiki Miyahara | "Counterfeit Coin Problem Can Be Extended to Secure Multiparty Computation" |
| El Hadji Mamadou Dia, Walid Arabi, Anis Bkakria and Reda Yaich | "StrawHat: Private Non-Interactive Gradient Boosting Decision Tree Evaluation Based on Homomorphic Encryption" |
| Nicolas Quero, Renaud Sirdey, Aymen Boudguiga, David Pointcheval, Quentin Sinh and Nadir Karam | "Scalable privacy-preserving database queries with FHE and PEKS" |
| Marc Damie, Mihai Pop and Merijn Posthuma | "Energy Consumption of TLS, Searchable Encryption and Fully Homomorphic Encryption" |
| Augustin P. Sarr | "An Embarrassingly Parallel Cryptanalysis of EC(H)MQV" |
Session 7: Secure and Intelligent Network Architectures for Next-Generation Communications
Session Chair: Omar Mawloud
| Alex Pierron, Michel Barbeau, Luca De Cicco, Jose Manuel Rubio Hernan and Joaquin Garcia-Alfaro | "A Fairness-Aware Strategy for B5G Physical-layer Security Leveraging Reconfigurable Intelligent Surfaces" |
| Lucas Schrass, Yu Shen and Stefanie Roos | "Anonymous Proactive Distance Vector Routing in Connectivity-Restricted Environments" |
| Andrea Fulgence Ndreveloarisoa, Frédéric Guidec and Mawloud Omar | "A secure lightweight system based on device-to-device communication for objects sharing in local communities" |
| Matthew Bush, Dave McKay and Atefeh Mashatan | "Consumer Zero Trust: Towards a Principled Adaptation of Zero Trust for Consumer Networks " |
| João Vitorino, Daniela Pinto, Eva Maia, Ivone Amorim and Isabel Praça | "Revisiting Network Traffic Analysis: Compatible Network Flows for ML Models" |
| Hocine Attoumi, Etienne Gael Tajeuna and Mohand Said Allili | "Causal Graph Modeling of Network Traffic for Early Cyberattack Prediction" |
Session 8: Secure, Explainable, and Efficient Machine Learning in Cybersecurity
Session Chair: Francoise Sailhan
| Ananta Raha, Junaeid Ahmed, Md Shohrab Hossain and Suryadipta Majumdar | "Defending Model Inversion Attack Using an Improved Filter-Based Approach" |
| Muhammed Tahir Akdeniz, Zeynep Yesilkaya, Ibrahim Enes Kose, Ismail Ulas Unal and Sevil Sen | "VOLTRON: Detecting Unknown Malware Using Graph-Based Zero-Shot Learning" |
| Alexandre Dohin, Karim Zkik, Omar Mawloud and Abdellah Akilal | "Deep Learning-Driven Energy Auditing for Smart Grid Cyberattack Detection" |
| Saba Kasrelou, Samuel Pierre and Ranwa Al-Mallah | "Verifiability of Unlearning Schemes Through Local Explanation" |
| Myria Bouhaddi, Feriel Sadoun and Kamel Adi | "Anomaly-Aware Aggregation for Robust Peer-to-Peer Machine Learning" |
| Shuaishuai Liu, Gergely Acs and Gergely Biczók | "Interdependent Privacy in Smart Homes: Hunting for Bystanders in Privacy Policies" |
| Daphnee Chabal, Dolly Sapra, Cees de Laat and Zoltan Mann | "QUOKKA: Faster Secure Neural Network Inference with Early-Exit Technology" |